First and foremost, I would suggest you to read my introductionary article on Monero to familiarize yourself with the different concepts that are introduced in Monero. You can read that article here: http://weuse.cash/2016/11/24/introduction-to-monero/
All these concepts come together in this picture (click to enlarge):
Bob wants to spend XMR he received in his account and send it to Carol.
How does he compose the transaction?
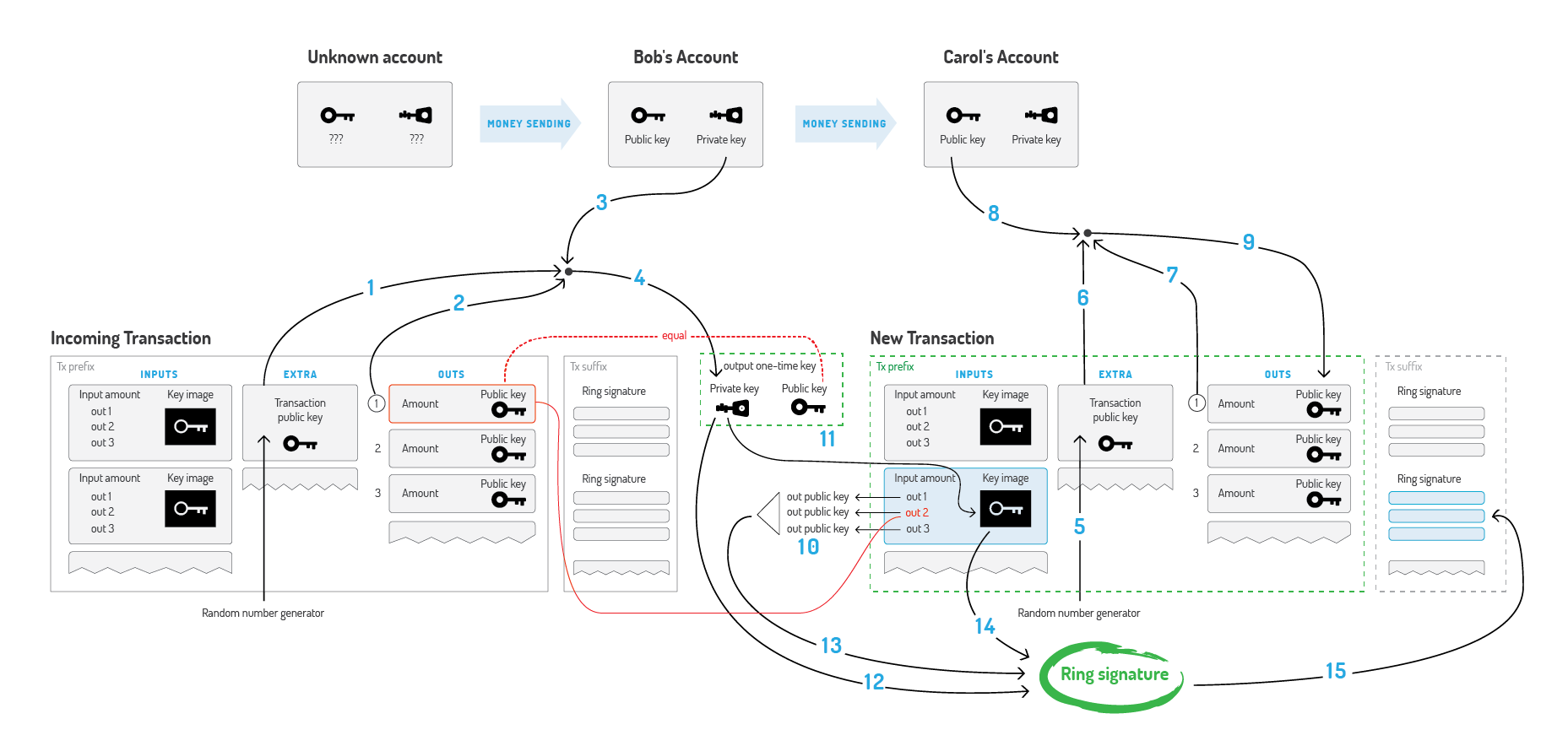
Back in 2015, I tried to come up with a good guide on what the different numbers actually mean in laymen terms. (Note that RingCT is not included.) Core dev Luigi1111 corrected a few things and expanded it a bit:
A: Bob gets access to his “real input” that was send to his “stealth address”.
1. Bob needs the public key from the transaction that contains the output he received and wants to send (Bob needs to “ECDH” this key with his private view key).
2. Bob also selects the exact number (index) of the output from the transaction that contains the output he wants to send. The other output(s) in this transaction is/are change (Bob doesn’t have the private key for those other outputs)
Note: typically, due to auto-denomination, Bob will have more than one output per transaction that belongs to him. This will change with RingCT, when denominations aren’t necessary anymore for ring signatures to work.
3. Bob needs the private spend key of his account.
4. 1,2 and 3 are used to calculate the private key for the specific output he wants to send. The public key for the transaction can be calculated from this private key and will be stored on the blockchain.
B: to protects Carol’s identity, Bob will do the following to generate a “one time” public key for this transaction, making it impossible for others to link all transactions send to Carol to the same “stealth address”.
5. Bob generates a random scalar.
6. This random number is the transaction private key, and is scalar multiplied into the transaction public key.
7. Bob selects the number (index) associated with the outputs (due to auto-denomination) that Carol will receive, the other output(s) is/are change that goes back to Bob.
8. Bob needs the public view key from Carol to be able to send it to her stealth address. This can be derived from Carol’s Monero address.
9. 6,7 and 8 are used to calculate the public key for the specific outputs Bob wants to send.
C: To “mix” the inputs, Bob creates a ring signature.
10. Bob selects the actual public key + that output’s private key from the output he wants to send, but he also adds other public keys into the mix. These other inputs are the “fake inputs” which makes Monero untraceable.
11. To prevent double spending, Bob needs to send a valid “key image” together with the public keys of the inputs of the transaction. This key image will prove that that a real input is a part of the ring signature, without disclosing which one.
12. Bob signs the combination of inputs and the key image with his private key, proving the key image is valid (Bob owns the private key associated with the key image.) and thus that one of the inputs is used to generate this key image. As a spectator of the blockchain, we can’t know which of the used outputs is “the real one that is being transferred”.
13. This is the collection of outputs that is signed. He grabbed the “fake ones” from the blockchain. He doesn’t need permission from the owners for that. In more detail: the outputs are doing the signing. A hash of the trasaction prefix is “what” is actually being signed in the ring signature.
14. This is the key image Bob signed with his private spend key. If Bob ever tries to send the same output again, the exact same key image will be generated and thus the double spend will be detected.
15.Bobs private key (12) and the other chosen public keys (13) are used to create a ring signature; there will be one signature for each input, collectively making a ring signature. The key image (14) is an additional public key computed from the output private key that’s actually being spent. This is the full ring signature transaction.
